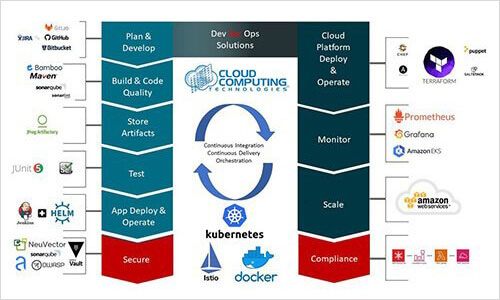
AWS DevSecOps Solutions
Overlooking security while working with DevOps is a recipe for disaster. Often, developers deploy applications in beta, but after finishing it, they fail to spin the instance down. Unfortunately, cybercriminals are always looking for these resources – it can serve as an entry point for cyberthreats. In order to prevent these issues, it’s important to add DevSecOps in the equation.
DevSecOps in the Mix
DevSecOps solutions are not only about security. It ensures that you incorporate security into the processes that you need for application development and ensures that security is added right into them by design.
Security with Automation
Service-Disabled Veteran-Owned Small Business (SDVOSB)
Gaining the benefits of Secure Coding with DevSecOps
Deploy code with confidence and assurances
1
Reduce false positives
2
Create cohesive teams and cooperative enviornment
3
Single source of truth in deployment caos
4
Eliminate pen-test bottlenecks
5
Visibility for each team
6
Scale horizontally for high velocity and high volume
Small Disadvantaged Business (SDB)
Small Disadvantaged Business leads to enhanced innovation and creativity, as these businesses often offer unique perspectives and solutions shaped by their diverse backgrounds. Moreover, partnering with Small Disadvantaged Business can provide access to specialized skills and capabilities that might otherwise be overlooked, contributing to improved competitiveness and efficiency.
AWS Services for DevSecOps
Generative AI Software Integration
- Define security roles by using the AWS Identity and Access Management service. It defines the responsibility of all members in a product change. It doesn’t only restrict capabilities, but also ensures security is incorporated in the project tasks. Additionally, you can easily verify who applies changes by checking configuration repositories like AWS CodeCommit or Git or going through audit logs.
- AWS Key Management Services (KMS) is helpful for developing and handling encryption keys required for protecting data. In addition, KMS guarantees your keys’ security by validating hardware security modules.
Transforming for Innovation and Sustainability securing future competitive advantage
What clients say about Cloud Computing Technologies







Transforming for Innovation, Sustainability and Security
- AWS CodePipeline is a powerful service for continuous integration and continuous delivery that enables DevOps to automate detective and preventive security controls.
- With CloudFormation, you can explain and provision infrastructure resources through a basic text in a secure and automated way. This service allows you to design your demo pipeline’s secure template.
- AWS Lambda takes the template of the CloudFormation and performs static code analysis. For your security groups in the scope, you can also execute dynamic stack validation.
AWS DevSecOps Consulting
We at CCT, introduce security early in the DevOps workflow with our AWS DevSecOps Consulting. Our experts possess all the necessary certifications and skills that can allow them to integrate AWS DevSecOps in your CI/CD pipeline and streamline your custom applications’ delivery.