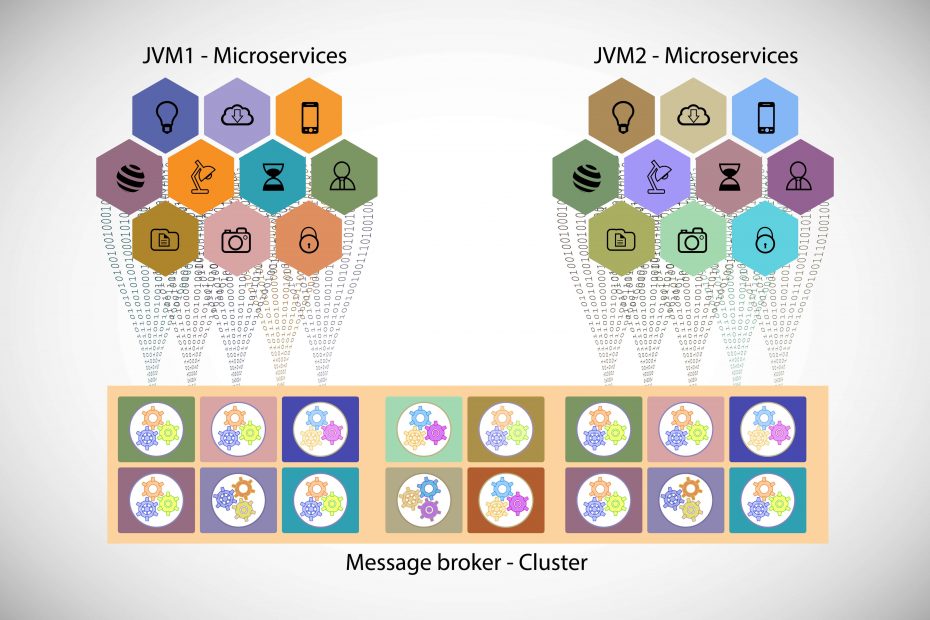
How Kubernetes Zero-Trust Security protects the Most Sensitive Data?
In the brim of maturation of clouds, containerization, microservices, and distributed applications, zero-trust security is in the hype of conversation in the IT world. Gartner is predicting that by the year 2022, 75% of the global organizations will be running containerized applications in production which may essentially and simultaneously follow container orchestration systems- Kubernetes as well commonly in most application… Continue readingHow Kubernetes Zero-Trust Security protects the Most Sensitive Data?