DEVSECOPS CONSULTING WITH SECURE CODE PIPELINE, GITOPS, AND SECURE CI CD

Small Disadvantaged Business (SDB)
Small Disadvantaged Business leads to enhanced innovation and creativity, as these businesses often offer unique perspectives and solutions shaped by their diverse backgrounds. Moreover, partnering with Small Disadvantaged Business can provide access to specialized skills and capabilities that might otherwise be overlooked, contributing to improved competitiveness and efficiency.
Service-Disabled Veteran-Owned Small Business (SDVOSB)

Transforming for Innovation, Sustainability and Security
Certified AWS DevSecOps Consulting Services
DevOps In The Cloud With Amazon AWS
- Rapid Development and Deployment of Applications
- AWS Managed Services
- AWS Cloud Platform as a Service
- Infrastructure as code
- Hyper-Scale Applications
AWS Cloud DevOps In Practice
- Plan, Build, Test, Release, Monitor
- Rapid Delivery
- Scale and Reliability
- Application Programming Interface (API)
- Security as Code
Agile Development
- Agile Methodologies
- 1 Week Sprints
- Continuous Integration
- Modular and Repeatable
- Scaled Agile and Trains
Containers
- Docker
- Kubernetes
- Resource Management
- Agile Developments
- Digital Factory
AWS Cloud Microservices
- AWS Fully Managed Services
- Service-Oriented Architecture
- Continuous Delivery
- Continuous Deployment
- Independently develop and deploy services
Cloud DevOps Tools
- Chef
- Puppet Labs
- Ansible
- Jenkins for CI
- Github
- Nagios
- Graphite
Transforming for Innovation and Sustainability securing future competitive advantage
Common Tasks Of An AWS DevSecOps Include
- Reviewing AWS infrastructure architecture and suggesting improvements
- Creating and scripting deployments for new and updated services
- Managing Ansible playbooks and repositories
- Managing Ubuntu and other Linux systems
- Optimizing Ngnix, Memcached, and Varnish for performance
- Integrating third-party applications into our platform
- Ensuring and monitoring infrastructure and platform compliance with strict security policies
- Coding in PHP, Python, and Ruby
- Debug issues with LDAP, CAS, Shibboleth and/or SAML SSO user authentication
- Designing and implementing backup, monitoring, and disaster recovery solutions
- Managing and tuning IAM, EC2, RDS, EMR, Lambda, API Gateway, Kinesis, DynamoDB, SQS, and other AWS services
- Managing and tuning MySQL, PostgreSQL, and other databases- Managing and tuning Hadoop clusters
- Zero Trust, Risk Management, and Secure CI/CD pipeline

CCT’s DevSecOps Consulting
Integrating Security into Your Code Culture
The Need for Adding Security to DevOps
- Cybercrime related damage is expected to cross $6 trillion annually by 2021?
- More than half (55%) of large companies are not effectively stopping cyberattacks
- The average cost of a breach is nearly $4 million?
Many companies aren’t including security in their development process, making themselves vulnerable to insider threats, malware, backdoors, and improper configuration. This is where DevSecOps brings terrific value to the table.
CCT’s DevSecOps CI CD Approach
- Code analysis – We speed up the rapid identification of vulnerabilities via code delivery in small chunks.
- Change management – We enables users to submit changes for increasing efficiency and speed and find whether the change’s impact is positive or negative.
- Investigative threats – Potential risks can emerge in any code update. We spot these threats early and neutralize them effectively.
- Monitoring compliance – Companies should comply with latest regulations, such as CCPA, PCI DSS, and GDPR. We prepare them for audits at any time based on the industry, state, and federal regulations.
- Training – We train your company’s IT and software engineers with security training and guide them to write secure code.
Generative AI Software Integration
AWS DevOps Developers Automate AWS Security At Web Speed!
Best Practices Approach to DevSecOps Consulting
Six major considerations for a security practical approach.
1 Code Analysis
Automated identification of vulnerabilities
2 Change Management
Determine the impact of changes on security
3 Visiblity
Monitoring to validate compliance
4 Investigations
Respond to threats from early identification
5 Perodic Assessments
Filtering for emerging threats
6 Knowledge Transfer
Training to empower security outcomes
Your Cross-Functional Experts In Development And Operations To Create And Deploy Your Enterprise Applications

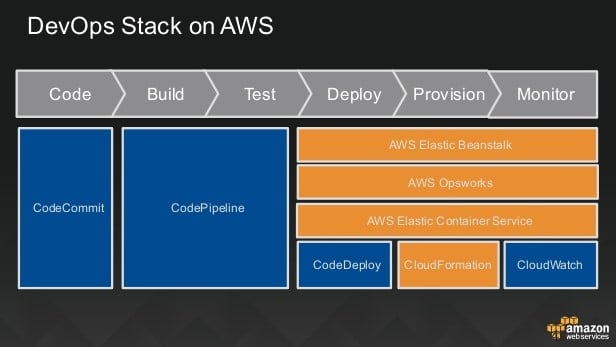
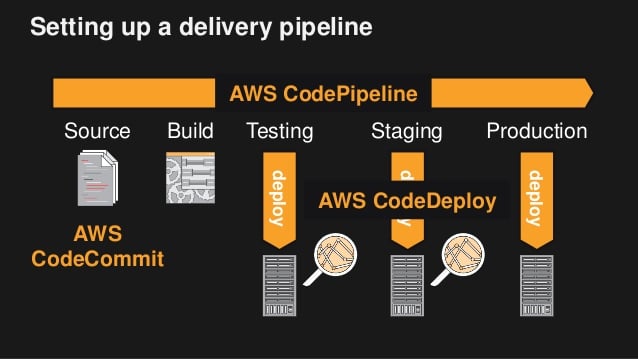
AWS CodePipeline
AWS CodeBuild

AWS CodeDeploy

AWS CodeStar
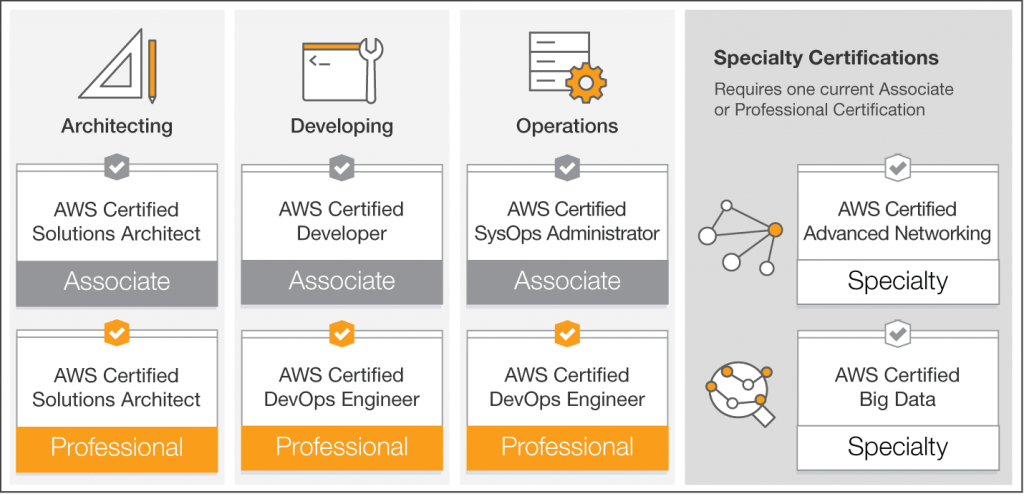
Our AWS DevOps Developers Have Certifications In:





What clients say about Cloud Computing Technologies






Benefits of Secure Code Pipeline
Reduce Time on Configuring Security Consoles
Enable Innovation
Identify Vulnerabilities
Reduce Legal Liability
Detect Loopholes in Open-Source Code
CCT’s integrated Secure Code Pipeline DevSecOps strategy incorporates automation, so developers aren’t using any open-source library that contains vulnerabilities.
Experience and Agile Expertise
CCT’s DevSecOps Process
Once you subscribe our CI CD services, we initiate work by following these steps.