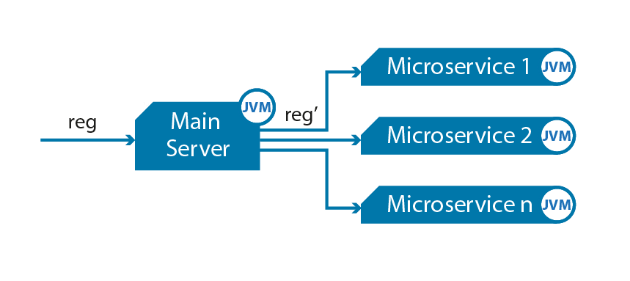
How to Keep Complexity Out Of Microservices
Microservice-based systems are gaining popularity in the industry. It is not strange given the potential of short development times, continuous deployment cycles, and a scalable, impactful component model for software systems. However, there is a downside. Things can quickly spiral out of control. How do you maintain control as the number of microservices, messages, and interconnections between them grow? How… Continue readingHow to Keep Complexity Out Of Microservices